What is certificate?
Normally we use certificate for security but remember that this will not provide a guarantee, because these are many other factor in security chain.
Certificate usage why we need certificates?
1. One of thing that you need certificates is for signatures, for example you are writing code for your software you can use the certificate for your code, without certificate no can modify your code. You can also sign your hardware driver for your product so that no one can made modification in your driver. We can also use certificates for emails through with you can confirm that an email comes from right source.
2. Internet traffic like HTTPS, SSL is also using the certificates.
3. In our networks we use encryption, IPSEC and other security measure, here you can also use certificates using certificate authority or can also generate certificates from your local machine.
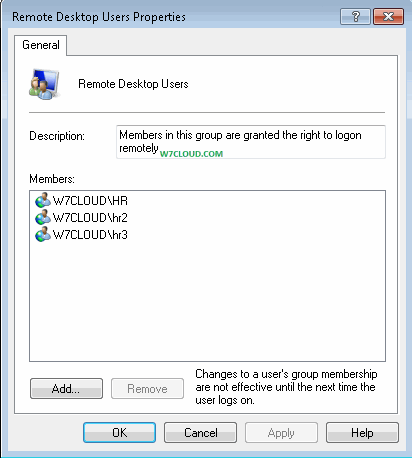
4. You can make your wireless communication more secure using certificates through which you can provide access to only those users who have a valid certificates.
PKI Hierarchy:
In Public key infrastructure there is a root CA which is primary responsible for issuing certificates. In down hierarchy there are some intermediate certificate authority machines, in below figure there are two computers one is issuing certificate for other computer and users. And in down hierarchy there are different CAs which are getting certificates from intermediate CAs. In this hierarchy if the root CA is generating certificate and all users and computer get and validate their certificate by following chain hierarchy from down to top. Root CA job is to only generate certificates to intermediate CAs and once intermediate CAs receives their certificates their job is to generate certificates to CAs down in hierarchy. And once all got certificate it is better to switch off Root and Intermediate CAs because intermediate certificates are normally valid for five year and in case of Root CA it is 20 years which is a long duration so for security purpose it is better to install Root and intermediate CAs on virtual machines.
Root CA and intermediate CAs are standalone certificate authorities and normally these machine are not a member of active directory also they are don’t have ability to automatically put the certificates in active directory. On the other hand Issuing CAs are called enterprise CAs they have the enterprise edition OS and member of active directory or domain. These CAs remain constantly online and provide certificates.
You can learn more about Installing AD Certificate services Role.