Taking a job interview related to AWS security can be challenging. There are many steps involved in the AWS interview, and it’s essential to be aware of the abilities needed to be successful for this position.The interview process can be daunting, with questions that seem impossible to answer. But don’t worry, we’re here to help.
AWS Security Interview Questions
One of my friend appeared for an AWS interview a few months back, and i have arranged a discussion regarding his interview. According to him, it was a tight interview, and most of the questions were related to Networking, Security, content delivery network, data Encryption and Distributed Systems. Using his experience we have compiled a list of the most asked aws security interview questions and detailed answers. The will help prepare for your interview, and you will feel assured that you’ll be able to conquer it .
What is aws?
Amazon web services (AWS) is a cloud platform that provides customers with a broad set of global cloud computing services. These include computing, storage, databases, analytics, networking, mobile, and development tools. AWS is an complete and advanced cloud computing platform.
What are necessary precautions required before migration to the AWS Cloud?
This is a general question and it will check you knowlegde about different swcurity aspect regarding AWS cloud migration. Before transferring into the AWS cloud, the users of these systems must concentrate on the following areas:
Security: Concentrate on your AWS account’s security and ensure that only authorized people can access it. Also, make an extremely strong and secure password to access your account and do not give it out to anyone.
Data: Migrate only the needed data and ensure that all the data is backed up before migration.
Cost: When you are workin in a company cost calculation is a very important task. Make sure you choose the suitable AWS pricing model for your needs so that you don’t spend more than you have to.
Capacity: Select the appropriate capacity based on your requirements to ensure that you don’t end with too much or small.
Connectivity: Make sure that you have good connectivity to the internet so that you can access your AWS resources.
Support: Make sure you have a good support system to get help.
Explain Amazon Guardduty?
If you are looking for job related to aws sercurity then guardduty is essisentail concept to understand. Amazon GuardDuty an alert service that constantly checks for suspicious or illegal activities in your AWS environment. It gives you a complete information about your AWS account’s activity, which includes actions performed by the account’s users, roles, and other services. GuardDuty also analyzes resource configurations and Access Control Lists (ACLs) to help you identify resources that are exposed to the internet or have excessive permissions. GuardDuty can generate alarms when it detects malicious or unauthorized activity so that you can take immediate action to protect your resources.
What are some of the best practices for security in AWS?
Again it is a broad and general question and every profression can explain it according to his own experience. But here are some of the best practices for security in AWS are:
– Enable the access control using IAM.
– Utilize MFA to provide an additional protection to the security of your AWS accounts.
– Use proper encryption methods to protect your data.
– CloudWatch is a great tool to monitor activity within the AWS system.
– Use Amazon GuardDuty to detect threats in your AWS environment.
– And you can use amazon WAF to secure your web application from threats.
You may be asked for different aws terms, so we have included some basic concept as under
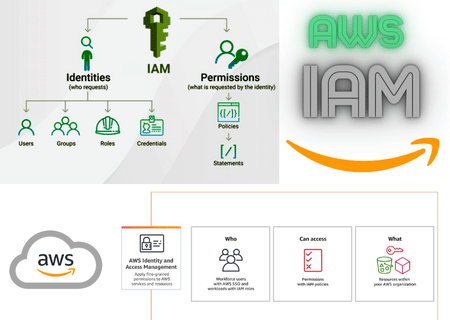
What is IAM?
IAM mean Identity, Access and Management. It’s a service that lets you manage access to AWS resources. IAM allows you to create groups and users and grant them permissions. IAM also lets you create roles and give them to users or groups. Roles are like permissions, but anyone with the role’s ARN can assume them. IAM is a critical part of security in AWS because it helps you control who has access to your AWS resources and what they can do with them.
What is MFA?
MFA is a stand for Multi-Factor authentication. It is a security protection that enables more than one type of authentication to gain access to an system. For example, you might use a password and a code from an authenticator app. MFA adds an extra layer of security to your AWS account by making it more difficult for unauthorized people to gain access. With this extra security method you can request a OPT code on email or on mobile number to access the AWS resource.
What is encryption?
The transformation of data is done by encryption so that those with the right key have the ability to only access it. Encryption is utilized to safeguard data during the process of transport and in rest. In transit, data is encrypted while transmitted from one location to another. Encryption is a critical part of security in AWS because it helps protect your data from being accessed by unauthorized people. AWS provide bydefault encryption on different services, but you can also enable the encryption using different services.
What are the types of data encryption methods used in AWS?
The following data encryption methods are available in AWS:
Server-side encryption:
Server-side encryption is a type of data encryption performed by the server. At the client end data is encrypted before forwarding whereas on server side it is decrypts back to orignal form.
Client-side encryption:
Client-side encryption is a type of data encryption performed by the client. The data is encrypted before it is sent to the server. The client then decrypts the data when it receives it.
Key management:
Key management is used to decrypt or encrypt the data. AWS provides several key management solutions, such as the AWS Key Management Service (KMS), AWS CloudHSM, and Amazon S3 Encryption.
What is cloud security in AWS?
AWS cloud security offers various features and services that can boost your capacity to meet the most important requirements for security and compliance, such as data protection, localization, and security. AWS can be used to automatize manual security processes so that you can concentrate on expanding and improving your business.
What are the Security Benefits of AWS?
Following are some key benefits of AWS cloud and security:
Data Protection:
To protect your data, AWS provides various features and services like storage and computes capacity, security, compliance, backup, and disaster recovery.
Cost-effective:
AWS gives you the ability to pay for only what you use. It is not necessary to purchase expensive hardware in the beginning . You can also save on operational expenses as you don’t need to hire a separate team to manage your infrastructure.
Multiple security solutions and software at AWS:
AWS offers a wide range of security solutions and software to secure your data and applications. These include firewalls, intrusion detection and prevention systems, data encryption, and more.
Scale Quickly and Elastically:
AWS allows you to scale your resources up or down as needed. It can be accomplished easily without any advance investment.
AWS compliance programs:
AWS offers a variety of compliance programs that will help you to meet your regulatory needs. These include the AWS Compliance Program, the PCI DSS Compliance Program, and the ISO 27001 Certification Program.
What are the key components of AWS Security?
The key components of AWS Security are:
Identity and Access Management (IAM):
As describe earlier that IAM is a web-based service that lets you create and manage groups and users and give them access rights.
CloudTrail:
CloudTrail is an online service that lets you keep track of the changes made that occur to AWS resource. It records all API calls made in your AWS account, including calls made by IAM users, roles, and federated users.
Amazon GuardDuty:
Amazon GuardDuty is a web service that is helpful for detecting & responding to threats in your AWS account. It provides a list of suspicious activities detected in your account and recommendations for responding to them.
AWS Config:
AWS Config is a web service that helps track changes to your AWS resources. It provides a complete history of all the changes made to your AWS resources, including which users made the changes and when they were made.
Amazon Inspector:
Amazon Inspector is a web service that helps you assess the security of your AWS resources. It provides a detailed report of all the security findings and recommendations for fixing them.
Amazon Macie:
Amazon Macie is a web service that helps you protect your data in the cloud. It uses machine learning to automatically discover, classify, and protect sensitive data in your AWS account.
What kinds of services are available to create a centralized log solution?
The essential services you can utilize include Amazon CloudWatch Logs stored in Amazon S3 and then Amazon Elastic Search to show the data. You can make use of Amazon Kinesis Firehose to transfer information from Amazon S3 to Amazon ElasticSearch.
What are Amazon CloudWatch logs?
Amazon CloudWatch Logs is a web service that helps you monitor and troubleshoot your systems and applications. It provides you with logs that contain information about your AWS resources, applications, and services. You can also keep track of your logs in real-time for specific words or patterns using CloudWatch Logs. You can find out the more AWS CloudWatch job related interview questions here.
Explain CloudWatch vs. CloudTrail?
CloudWatch is a monitoring tool for AWS applications and resources, in contrast, CloudTrail can be described as an online service that records API activity within Your AWS account. Both are excellent monitoring tools within AWS. With CloudWatch, you can gather the metrics you want to track, collect and analyze log files and create alarms.
What is Amazon CloudFront?
Amazon CloudFront is a global content delivery network (CDN) service that accelerates the delivery of both static and dynamic web content, like videos, images, as well as applications.
It provides a secure and reliable way to deliver your content to end users with low latency and high availability. CloudFront distribute your content through worldwide with internationally distributed cache servers. When a user requests your content, its request sent to the nearest edge location, which provides the lowest latency.
Explain the term AWS Shield?
The AWS Shield is used to handle the DDoS security service. It offers greater security against DDoS attacks on the AWS resources, such as Amazon EC2 instances, Route 53 resources, and Elastic load balancers for load balancing. This AWS Shield you can access to AWS WAF, a firewall for web applications which helps safeguard your web-based applications from exploits that are common to all.
What is AWS WAF?
AWS WAF acts as a firewall for web applications which helps safeguard your web-based applications from exploits that are common to all web applications. AWS WAF provides a set of rules that you can use to block or allow traffic to your web applications. These rules are based on the characteristics of the traffic, such as the source IP address, URL, and web request type.
What are the benefits of using AWS KMS?
AWS Key Management Service (KMS) is a managed service that makes it easy to create and manage keys. It is highly available and scalable and provides many features, such as auditing, key rotation, and more.
What are the benefits of using Amazon S3 Encryption?
Amazon S3 encryption provides some benefits, including:
- Data is encrypted using server-side encryption at-rest (EAR) with either AWS KMS or Amazon S3 Encryption Keys.
- SSL/TLS is used to encrypte the data in in transit.
- Amazon S3 handles the key management for you.
- It is highly available and scalable.
- With S3 encryption is transparent to users and applications.
What are the benefits of using Amazon Inspector?
Amazon Inspector allows you to assess the security of your AWS resources. It provides a detailed report of all the security findings and recommendations for fixing them.
What are the benefits of using Amazon Macie?
Amazon Macie is a web service that helps you protect your data in the cloud. Machine learning is used to detect the type, classification, and security of sensitive information in your AWS account.
How can I protect my AWS account from security risks?
There are several ways to protect your AWS account from security risks. These include using strong passwords, creating IAM users and roles, using multi-factor authentication, and more.
Concusion:
The AWS Cloud is revolutionizing the way businesses manage their IT infrastructure, and more and more companies are embracing the cloud with open arms. AWS offers a wide range of services and products, and AWS security covers a lot of ground. But how much do you know about these security measures? AWS offers a lot of information on their website, but you can’t know everything. That’s why we have created this list of AWS security interview questions for you to study before your next interview. We hope you find the questions useful and that your next interview goes well!.
It will be very helpful for our readers if you share your interview experience in the comments. Thanks!