Port Forwarding with SSH | Types of Port Forwarding
SSH Port-forwarding is a technique used to send/forward data across the VPN. Data to be transfered to a specific port of a local PC can be send to a particular-port of a remote-system using a separately prepared tunnels or communication pathway. For using SSH protocol you can use the SSH clients software.
Today we use VPNs (Virtual Private Network) in order to access computers / servers on a private network. One of way to accessing the private network is SSH, SSH also provides access to these private networks. Indeed, SSH makes it possible to “forward” ports, that is to say, like a router, to make port forwarding. The following three main types of port forwarding in ssh are available:
- Local port forwarding
- Remote port forwarding
- Dynamic port forwarding
What is Local port forwarding?
Local port forwarding allows you to redirect one of our ports to a remote machine. Thanks to this method, with the ssh protocol, you can access any machine of a VPN containing a ssh server open to the public. The syntax of the command will be:
ssh -L <localport>: <remote_ip>: <remote_port> user @ host
Here is an example to illustrate this command. Consider the following diagram:
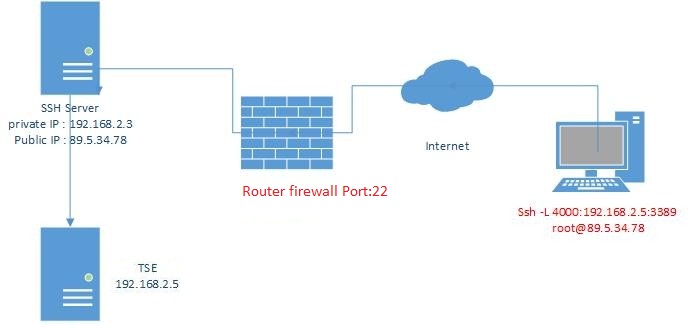
We therefore want to access the TSE server in order to have access to the remote office. We will therefore use the following command: ssh -L 4000: 192.168.2.5: 3389 [email protected]
More in detail :
-L to tell ssh that we want to do a local port forwarding, that is our local port will be redirected.
The ‘4000’ corresponds to our local port, the one we want to redirect to the remote port. We could very well have port 3389 if our port was free, but for purposes of illustration and understanding I chose port 4000.
The IP address 192.168.2.5 is the IP of the remote machine that you want to access. If for example we wanted to access an open port only locally on the ssh server, we would have put “localhost” or 127.0.0.1.
The ‘3389’ is the remote port on which we want to redirect our local port.
It will now be sufficient to connect to the local port 4000 to access the shared office of the TSE server. Local port forwarding can also be very useful on machines that have firewalls or listen only on their loopback interface, ie 127.0.0.1.
The local port forwarding allows us to access a remote network through an ssh server. However, what if we want to give access to our network?
Remote Port Forwarding
This is very similar concept to the Local port forwarding. Unlike local port forwarding, remote port forwarding allows you to redirect one of our local ports to a remote ssh server.
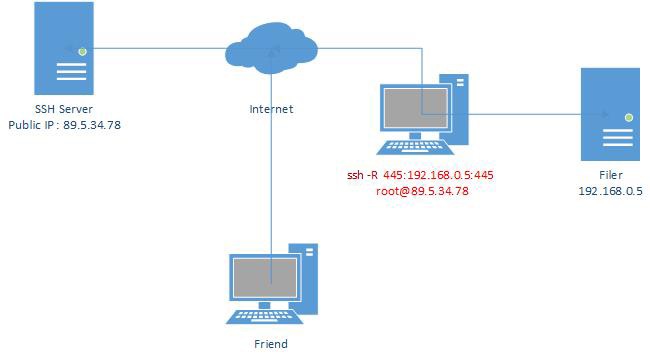
Here is an example of where we could use it: you have created a website still in development, you want to show it to a friend. Except, you can not or do not want to do port forwarding. You will be able to redirect your local port 80 to a remote ssh server.
The syntax of the command is very similar to the previous one:
ssh -R <remote_port>: <local_ip>: <local_port> user @ host
We want it to be the remote machine that accesses a machine from our local network. Or from another point of view, give access to a service from our local network to one or more people.
In the above example, we want to make a sharing server accessible.
We will therefore use the following command: ssh -R 445: 192.168.0.5: 445 [email protected]
The -R option tells ssh that we want to do remote port forwarding.
The first ‘445’ is the port of the remote machine that will be redirected.
192.168.0.5 corresponds to our file sharing server. We could have put “localhost” if we wanted to redirect one of our local port, to make accessible one of our shared folders.
The last ‘445’ is the port of the local machine that we want to redirect.
Our friend will be able, with a local port forwarding to have access to the sharing. It’s also possible that the ssh server is on this friend’s local network, so it will just have to connect to the ssh server as if it’s a file server.
The Dynamic Port Forwarding
The dynamic port forwarding is different from local and remote port forwarding. We will use here a complementary utility called proxychains. Proxychains is a SOCKS proxy, unlike an http proxy, it allows to redirect all our traffic to a remote machine and not just http requests.
Dynamic port forwarding will simply allow us to send all our traffic to a remote machine through a particular port. The proxychains utility will be used to redirect our traffic on this port, while ssh will handle the data transfer.
The order will be as follows:
ssh -D 9050 user @ host
Why 9050? We could indeed use any port, this port is chosen according to the configuration of proxychains located in / etc / proxychains.
The ssh server will act as a proxy. Proxychains also makes it possible to make “chains”. That is, to go through several proxies. The application of proxychains is not limited only to SSH of course, it is possible to use it to go through the TOR network.
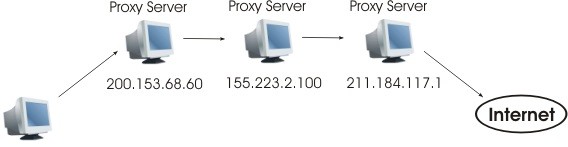
Then, for an application to use this proxy it will be enough to add “proxychains” before the command.
For example we can type: firefox proxychains. We will see, either with a dump of the traffic of our network or by checking the IP with which one reaches a web page, that one passes well by our or our servers ssh.
Conclusion:
The ssh command can do a lot of things. In addition to being secure, it makes it possible to create tunnels between different machines. It is also possible to create client / server and peer-to-peer vpns.
We can couple all of these options to the -N option that will allow us to not run a remote command and the -n option that redirects the stdin stream to / dev / null. This means that everything we type in the terminal will not be sent to the remote server but will be deleted. You should also know that all these options are valid for windows. Putty also helps to do it.













