NMAP Commands For Linux
This article is about the Nmap commands in Linux. A complete and details list of Nmap commands or Cheat Sheet for different types of port scanning. Nmap is an interesting and powerful Linux tool that can help us discover information about computers on the network. It use different scanning methods it offers and the various options. Nmap is created by Gordon Lyon and a very popular open source network scanner for both Windows and Linux.
Its helps system administrators to finds the list of clients connected to the network. It can find the following common information about the clients;
- Names of Computers
- what software is installed on them
- Their operating system
- What types of filters are used
- Information about the TCP and USP ports.
The can get the extra advantages using its scripting language, which allows administrators to automate many actions. The content of the article:
How Does NMAP Work?
In computer Lan networks, all connected devices have their own ip address. And ping protocol is support by each computer. Ping protocol can determine whether a computer is connected to the network or not. You are required to send a ping request to the computer, and if it responds, then we believe that it is connected. Nmap takes a slightly different approach. Computers also respond in a certain way to certain network packets, the utility simply sends the necessary packets and looks at which hosts sent the answer.
Every-thing on the command_line of Nmap that is not an option is treated as a target host-specification. The simplest-case is to define a target IP-address or host-name for scanning.
More interesting is how Nmap finds out what services are running on the machine. The essence of all network programs is based on ports. To receive a message from the network, the program must open the port on your computer and wait for incoming connections. And to send a message over the network, you need to connect to a different program (destination) port. Then the program will need to open the port on which it will wait for a response. The nmap utility scans the available range of ports during network scanning and tries to connect to each of them. If the connection succeeded, in most cases, by transmitting several packages, the program may even find out the version of the software that is waiting connections to this port. Now that we’ve covered the basics, we’ll look at how to use nmap to scan ports and networks.
Syntax for Nmap Commands
The Nmap launch command is very simple. To do this, just pass the destination IP address or network to it in the parameters, and also Now let’s look at the main options that we will need in this article.
- -sL – just create a list of running hosts, but do not scan nmap ports;
- -sP – only check if the host is accessible using ping;
- -PN – consider all hosts available, even if they do not respond to ping;
- -sS / sT / sA / sW / sM – TCP scan;
- -sU – UDP scan nmap;
- -sN / sF / sX – TCP NULL and FIN scan;
- -sC – run the default script;
- -sI – lazy Indle scan;
- -p – specify the range of ports for checking;
- -sV – a detailed study of ports to determine the version of services;
- -O – determine the operating system;
- -T [0-5] – scanning speed, the more, the faster;
- -D – mask scan using _ctitious IP;
- -S – change your IP address to the speci_ed;
- -e – use a speci_c interface;
- -spoof-mac – set your MAC address;
- -A – de_nition of the operating system using scripts.
Nmap Commands
Following Nmap Commands are discussed in this post:
- Basic Nmap IP or host Scan
- How to Scan a ports or scan multi ports with Nmap
- Save Nmap scan results to a text or xml file
- Scanning TCP or UDP ports with Nmap
- How to find or detect the operating system with Nmap in the Network
- Scanning with scripts NSE of Nmap
- Disabling DNS name resolution
- Nmap Get Information about HTTP services
- How to Scan the Firewall Settings on a Network Device
- Scan IPv6 Addresses with Nmap
- how to determind Host Interfaces, Routes, and Packets with Nmap
- Fast Scan of Host with Nmap
- How to find the open port with Nmap commands
- Check the number of packets send or received
- Detect service/daemon versions
- Nmap Scan for MAC address spoofing
- Launching DOS with Nmap
- Launching brute force attacks
- Detecting malware infections on remote hosts
- Timing and Performance

Nmap IP or host Scan Commands
You can use the following commands for scanning a IP address or host on the network.
Scan an IP:
nmap 192.168.1.110
scan a hostname:
nmap myhostnameScan a range of IP’s (in this case from IP 100 to 120):
nmap 192.168.1.100 - 120nmap scan subnet
Scan a subnet :
nmap 192.168.1.0 / 24Scan a list of goals from a file, where the file name is list.txt:
nmap - iL list. txtHow to Scan a ports or scan multi ports with Nmap
Scan single port with Nmap
nmap - p 22 192.168.8.109how to Scan a range of ports
nmap - p 1 - 30 192.168.8.109Scan the 100 most common ports with Nmap
The fastest option to run a scan with nmap:
nmap - F 192.168.8.109This type of scan uses the ports defined in the file
/ usr / share / nmap / nmap-services Scan all ports (65536):
nmap - p 192.168.8.109Save Nmap scan results to a text or xml file
You can save or export the commands results into a text file
nmap -oN output_filename.txt securitytip.comIf you want to save files into XML format with Nmap you can use the following Nmap commands:
nmap -oX output_filename.xml securityss.comScanning TCP or UDP ports with Nmap
You can perform different types of Nmap scanning for TCP and UDP ports . Let’s see what they are and their main differences. Scan with TCP Connect (a different type of scan that requires a full connection to the scanned ports, and this can cause a slower scan; usually the poll used is the SYN scan , which does not establish connections when scanning):
nmap - sT 192.168.1.102Scan with TCP SYN (the default scan type). It is characterized by being stealthy and little annoying; requires privileged access:
nmap - sS 192.168.1.102Scan UDP ports (to scan services over UDP instead of TCP , which is usually the most common):
nmap - sU - p 53 , 67 192.168.8.109With the previous line we will scan ports 53 and 67 UDP . 53 is the DNS port and 67 and 68 are those of DHCP . Scan ignoring the discovery (when the target computers, such as servers, ignore the PING ):
nmap - Pn - F 192.168.1.106How to find or detect operating system with Nmap in Network
Detect the Operating System and active services:
nmap - A 192.168.1.108Standard service detection (version detection, get more info of what is running once the ports have been detected):
nmap - sV 192.168.1.104Aggressive service detection (useful when services are running on ports that are not usual):
nmap - sV - version - intensity 5 192.168.1.1Lightweight service detection (a faster way to detect services):
nmap - sV - version - intensity 0 192.168.1.1Scanning with scripts NSE of Nmap
Inside the / usr / share / nmap / scripts directory
We can find a large number of predefined scripts to scan countless services or possible vulnerabilities in a system. Take a look at the directory and all available scripts because surely one of them catches your attention and is useful to you.
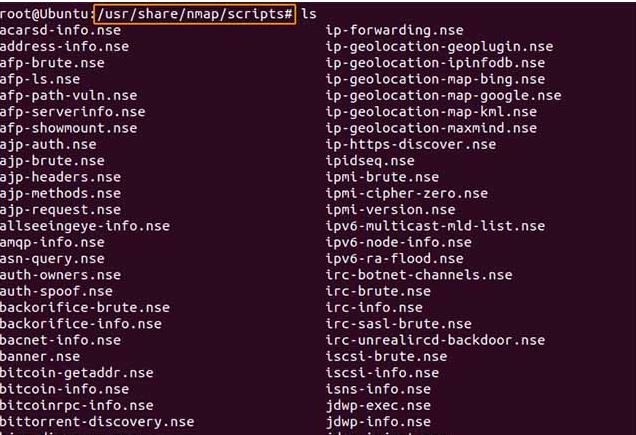
Help and information about scripts NSE of Nmap
With the option
- script - help = script_name We will get the help of each of the scripts, and some info about the usefulness of the script:
For example:
nmap - script - help = whois - domain. nse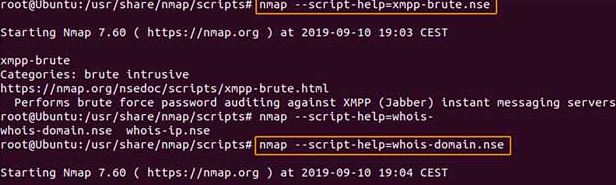
How to Disabling DNS name-resolution For fast Scanning Nmap
You can speed-up your Nmap scans a little bit, for this you need to choose the disable reverse DNS-resolution for Nmap scans. Just use the “-n” parameter in Nmap Commands.
[root@w7:~] nmap -p 80 -n 8.8.8.8
Starting Nmap 7.60 ( https://nmap.org ) at 2019-12-11 11:25 -13
Nmap scan report for 8.8.8.8
Host is up (0.014s latency).
PORT STATE SERVICE
80/tcp filtered httpSee the difference with a normal sacn without disabling DNS-resolution, or when DNS resolution is enable:
[root@w7:~]nmap -p 80 8.8.8.8
Starting Nmap 7.60 ( https://nmap.org ) at 2019-12-11 11:25 -13
Nmap scan report for google -public- dns-a.google.com (8.8.8.8)
Host is up (0.019s latency).Nmap Get information from HTTP services
In the directory / usr / share / nmap / scripts of nmap we can find about 129 different scripts to scan http . Let’s see some of the most classic scripts:
Find out the page titles of HTTP services :
nmap - script = http - title 192.168.2.0 / 24In this case we can see what you get when scanning a CentOS server with Apache running:
Collect headers HTTP :
nmap - script = http - headers 192.168.8.0 / 24We see that all the information of the HTTP header appears :
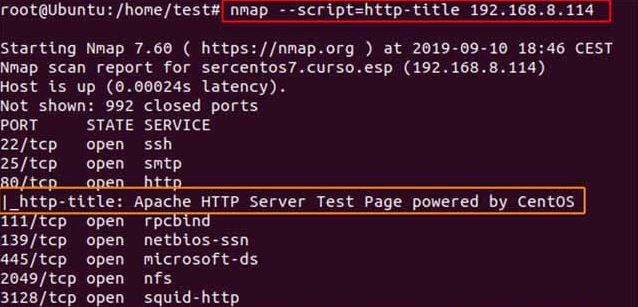
Nmap HTTP headers
Find web applications of known routes:
nmap - script = http - enum 192.168.8.114 This script searches application info on known routes; We see that in this case it has detected several :
nmap http-enum | known web applications and ruras
Find web applications of known routes:
| nmap – script = http – enum 192.168.8.114 |
This script searches application info on known routes; We see that in this case it has detected several potential directories.
How to Scan the Firewall Settings on a Network Device
With the Nmap you can detect firewall settings which can be use for penetration testing & vulnerability scans. You can use the following Nmap command for getting the firewall setting.
nmap -sA 192.168.0.1
Scan IPv6 Addresses with Nmap
IPv6 adressing is becoming more popular, and you can also scan Ipv6 address with Nmap. You can perform all Nmap commands of Ipv4 with IPv6.But a flag is required for IPv6 address to tell Nmap that this is not IPv4.
nmap -6 ::ffff:c0a8:1
Determined Host Interfaces, Routes, and Packets with Nmap
In network, some times you are required information of remote host like host interfaces, print interfaces, and routes. With Nmap you can easily achive this, use the iflist command:
nmap --iflistThe “–iflist” Nmap command will provide the list of the relevant host name, interfaces and routes.
nmap --packet-traceFast Scan of Host with Nmap
You can perform a fast scan of host or IP address using the following Nmap commands
nmap -F 192.168.1.1
nmap -T5 192.168.1.0/24 (for all devices on devices/computers for open ports ever)How to find the open port with Nmap commands
You can check or find the only open port on the target host and IP address with these Nmap Commands:
nmap --open 192.168.2.1
nmap --open blog.cyberweb.infoCheck the number of packets send or received
You can check the number of packets send or received by a host with Nmap command:
nmap --packet-trace 192.18.2.1
nmap --packet-trace blog.cyberweb.infoDetect service/daemon versions
You can detect remote services version numbers (server / daemon) with Nmap using this commands.
nmap -sV 192.212.2.1Output of Commands
Starting Nmap 5.00 ( http://nmap.org ) at 2019-09-12 11:14 IST
Interesting ports on 192.212.2.1:
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh Dropbear sshd 0.52 (protocol 2.0)
80/tcp open http?
1 service unrecognized despite returning data.Nmap Scan for MAC Address Spoofing
You can scan MAC address with different Nmap Commands
### MAC address spoof command ##
nmap --spoof-mac MAC-ADDRESS-HERE 192.12.2.1
### Use a random MAC address, The number 0, means nmap chooses a completely random MAC address ###
nmap -v -sT -PN --spoof-mac 0 192.12.2.1
### Add other MAC address Spoofing options ###
nmap -v -sT -PN --spoof-mac MAC-ADDRESS-HERE 192.12.2.1
Launching DOS with Nmap
Actively Exploit Detected Vulnerabilities with NMAP
With the NMAP’s exploit_script to find NMAP actively exploit detected-vulnerabilities, by using the following Nmap command:
nmap --script exploit -Pn Use NMAP to Brute Force Passwords
There are different Nmap scripts for brute forcing password, including oracle-brute, http-brute, snmp-brute etc. You can do this by issuing the following Nmap command to perform brute-force attacks to find out the authentication or password of a remote host or server.
nmap --script brute -Pn Test if Target Is Vulnerable to Dos with Nmap
You can use the following Nmap command to check whether the target is vulnerable to DoS:
nmap --script dos -Pn NMAP Commands to Perform DOS Attack
For DOS attack with Nmap, you can use the following command:
nmap --max-parallelism 750 -Pn --script http-slowloris --script-args http-slowloris.runforever=trueTiming and Performance
A default Nmap scan of a IP address on my LAN takes a 1/5 second. That is almost an enough-time to blink, but adds-up when you are scanning more host like thousands of hosts. As an experts security engineer you must aware that how to optimize the Nmap commands, which perform faster. Experience network engineer carefully craft Nmap commands to get only the info they care about while meeting their time-constraints. Optimizing Nmap commands parameters for time can also make a substantial difference. Techniques for improving scan-times include omitting non-critical tests, and upgrading to the latest version of Nmap.
Nmap Commands Examples
Following are some Nmap commands examples. With some real IP addresses and hostname are used to make things more concrete.
nmap -v cloudinfo.org
This commands scans all reserved-TCP-ports on the host cloudinfo.com. The -v option enables verbose mode.
nmap -sS -O security.org/24This SYN command scan against every host that is up out of the 256 IPs on sub-network.. It also tries to find which OS is running on each machine that is up & running. You are requires root rights for this commands.
nmap -sV -p 22,53,110,143,4564 198.116.0-255.1-127This command will launches host-enumeration and a TCP scan at the first half of each of the 255 possible eight-bit subnets in the 198.116 class B address space.
nmap -v -iR 100000 -Pn -p 80Asks Nmap to choose 100,000 hosts at random and scan them for web servers (port 80).
Last Words For Begginers
If you are interested in using and learning Nmap and you are feeling that Nmap commands are difficult to understand. Then there are some Nmap software are available which provide the GUI interface of Nmap and you can execute the different Nmap operations without using the Nmap commands. Zenmap is an example of such tool.