In Auto enrollment certificates are distributed automatically by certificate authority and user even not being aware that certificate enrollment is taking place. Normally certificates issued to computers and services are done by auto enrollment.
Here I will show you how you can auto enroll the user certificate using certificate authority in active directory. You need the following step to accomplish this task:
- Create and configure the Duplicate Template
- Assign read and write and Auto enroll Permissions
- Publish the Certificate
- Create a Group Policy for auto enrollment
For better understanding I want to share my network topology with you, I am using three systems for this task.
- Domain controller: w7cloud.com
- Certificate Authority Server: (ca.w7cloud.com) AD certificate services installed on it. You can learn more about installing Certificate services.
- W7-client: (w7-client.w7cloud.com) where we will test auto enrollment of the user certificate.
Create and configure the Duplicate Template:
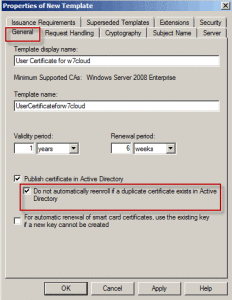
Go to certificate templates and create a duplicate template for “user” certificate by right clicking on user certificate, select windows server 2008 (as my clients are using windows 7) and give some name to this certificate. Creating Duplicate Template is also define in Key Archiving in Certificate services you can visit this for reference.
Once you create a duplicate certificate it will ask you for some setting and configuration, you can choose the setting according to you requirements but following are some important setting that you should keep in mind while creating duplicate user certificate template.
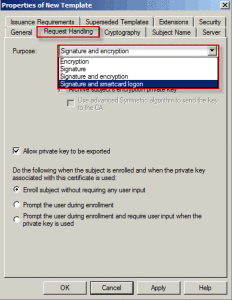
For example select the purpose of user certificate, I choosing “signature and encryption”.
From cryptography tab you can select the encryption type according to your choice. I am using RSA with 2048bit key size.
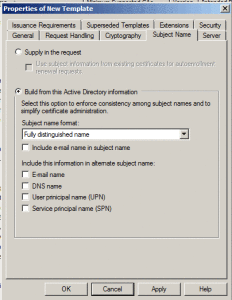
Be careful while selecting different checkboxes from “Subject Name “tab if you don’t specify the email for users then it is better that you don’t select the email checkbox otherwise this client or user may not receive the certificate.
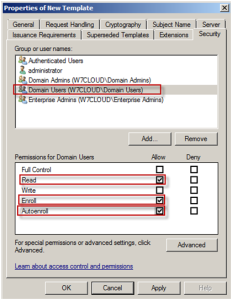
Other important thing for user template is to assign the “enroll” and “Autoenroll” right to domain users from security tab so that domain user can get certificates.
Click Apply and ok and you will find your certificate in certificate template under your CA server.
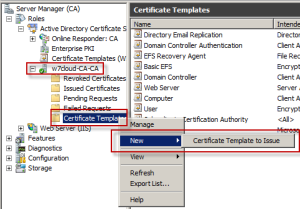
Publish the Certificate
To add this certificate to active directory users, right click on certificate template under your domain and click on new certificate template to issue. And select your user certificate from certificate list.
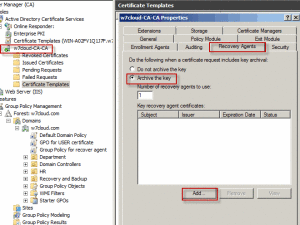
Right Click on domainproperties and then from “Recovery Agent” tab select archive this key and add your certificate from add button.
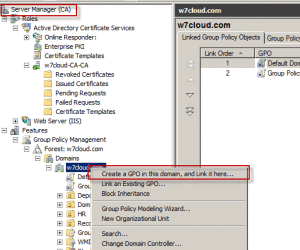
Create a Group Policy:
Now I have created a group policy for auto enrollment of user certificate for active directory user. You can create a group policy by right click on your required domain from features/group policy management and choose the first option “Create a DPO in this domain and link it here”. You can learn how to add/create Group Policy in Active Directory
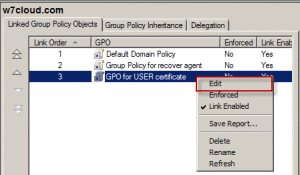
Choose a name for GPO and click on OK. Now right click on newly create Group Policy and click on Edit for defining your own setting.
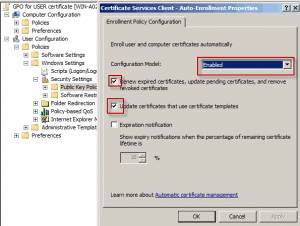
From user configurationpolicieswindows settingssecurity settingsPublic key policies enable “Certificate Services Client-Auto Enrollment”.
Now for test login into your client using a domain user and open MMC and add the snap-in from file menu and add the certificate snap-in and click OK. There in personal/certificate folder you will find your user certificate.
Note: You may not find the certificate at your first login into client machine, you can try following steps for troubleshooting:
- Restart client computer
- Run the command GPUPDATE and certutil –pulse in administrator command prompt.