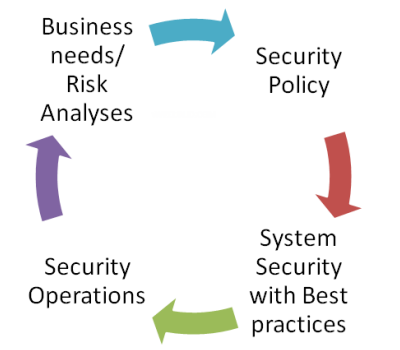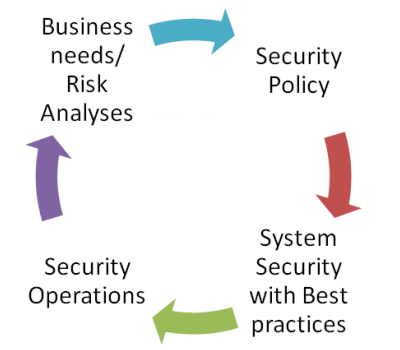
Network security System Life Cycle:
As a Design professional security is one important aspect of job and as a CCDA candidate you should know about the security policy that is a key aspect of an organization’s network design. To offer the level of security that you need to enhance the network confidentially, integrity and Authenticity, security policy is a key element to secure your network services. Security policy is the written guideline and standard for your network security.For example you have internet usage policy, access control policy and email policy. Security policy defines the architecture for your network like you are using IPSec or some other protocols. You can use the following life cycle for implementing the security to your network. The first of network security life cycle is to determine the busing needs and requirement and then you need to find out all the possible risks related to your network security. You can use the penetration testing with some tools for vulnerability scanning.
Then the next step in security life cycle is “security system” like port base security, IPSec or AAA server etc. and security operation integration and implementation of security services and monitoring. You can also go back and again modify and define the business needs and other sequential steps of security life cycle.
Security Policy:
Security policy is the written rules of your network security, you can make a security policy by following these steps:
- Define a Security Policy
- Methodology use for implementing that policy
- Component of security policy
- Risk Assessment
Define a Security Policy
RFC 2196 define a standard security policy that define the rules and regulations for employees and contracture whenever they access the company’s data and systems the rules and guideline must be abide by. It is overall general framework for your organizational security implementation so it is a complete document that defines all part and module of your network. Another important part of security policy is to define the responsibilities and limit of every person and also identify methods and procedures those would be follow when someone violate the security policy. You can create a committee for implement of the security policy.
Methodology use for implementing that policy
Cisco defines the five step methodology for implementation of security policy.
- Identify components and resources of network to protect
- Determine the all possible threats
- Risk assessment
- Implement cost effective migration
- Review and create the document of whole process
Component of security policy
Some of common and important components of a security policy include:
Acceptable use policy: which is basically an end user document written in easily understandable language that tell these are rules and regulations, define things that you can do and things that you can’t do and implement different limitation on users. For example most organizations limit the users from sending the company data to outside, also data-upload is restricted.
Network Access Control: Define the general access rules, thing like password strength, storing of password, classification of data like top secret and confidential data.
Security Management: In security management you can define how shall you manage the security policy, what type of tool will you use like “Cisco MARS” and 802.x.
Incident handling: how you going to handle the process and processors for managing incident handling. Things like network disaster plan and business continuity policy falls under this incident handling.
VPN Policy: VPN policy is an important component of network security policy for today’s world. You need to define the proper VPN type and system for creating VPN with proper encryption and IPSEC.
Physical Security: May be you need to define a proper physical security for your network according to your organizational requirements. For example restrict access to server room with biometric security. CCTV camera can also be part of your physical security.
Training of employees: For proper implementation of security policy you may need to create the awareness in employees, you can conduct training for new employees and also for old as well.
Risk Assessment:
There are two driving factors behind the security policy one is business needs and other is the risk assessment. You should have a proper risk assessment and need to define the minimum acceptable level of risk. Severity, control and probability are the three component of risk assessment. These components explain which asset you are going to secure, monitor the value of asset and actual loss in results if your network resources are down.
Risk assessments should explain the following:
- What assets to secure
- The monetary value of the assets
- The actual loss that would result from an attack
- The severity and the probability that an attack against the assets will occur
- How to use security policy to control or minimize the risks
The risk index is calculated by multiplying the severity times the probability factor, and then dividing by the control factor:
Risk index= (Severity factor * probability factor)/control factor